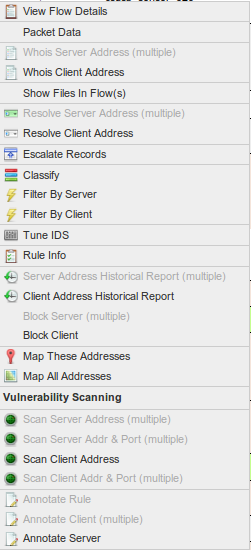
Forensic Tools
By right clicking a row in the Real Time or Historical summary reports, users can access the Forensic Tools in Figures 1 and 2 below. Summary View ("All") has a different set of menu options than Detailed View.
Contents
- 1 Forensic Tools
- 1.1 View Flow Details
- 1.2 Packet Data
- 1.3 Whois Server/Client Address
- 1.4 Show Files in Flow(s)
- 1.5 Resolve Server/Client Address
- 1.6 Escalate Records
- 1.7 Classify
- 1.8 Filter by Server/Client
- 1.9 Tune IDS
- 1.10 Rule Info
- 1.11 Server/Client Address Historical Report
- 1.12 Block Server/Client
- 1.13 Map These/All Addresses
- 1.14 Scan Server/Client/Port
- 1.15 Annotate Rule/Server/Client
Forensic Tools
This menu is context sensitive and only displays the options available for a particular record (row). For example, if a particular record has multiple server addresses, the Resolve Server Address option is not available.
View Flow Details
This shows all of the individual records that constitute the aggregate summary record.
Click on the button shown above to go back to the summary view.
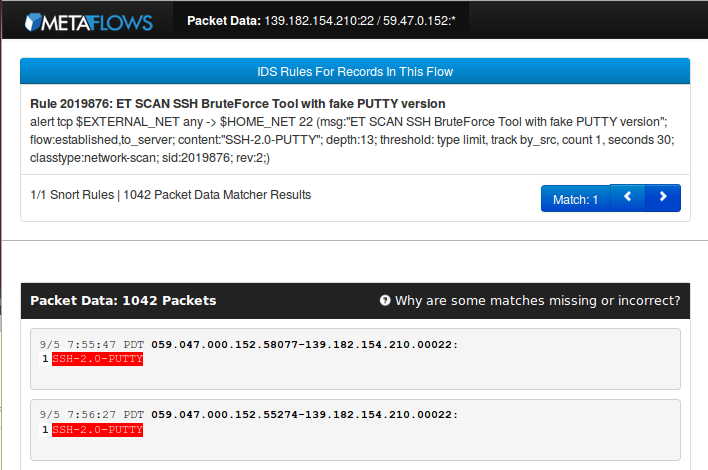
Packet Data
This retrieves packet data corresponding to the event. It will also show the IDS rules involved (if any) and will try to show why the rule(s) matched.
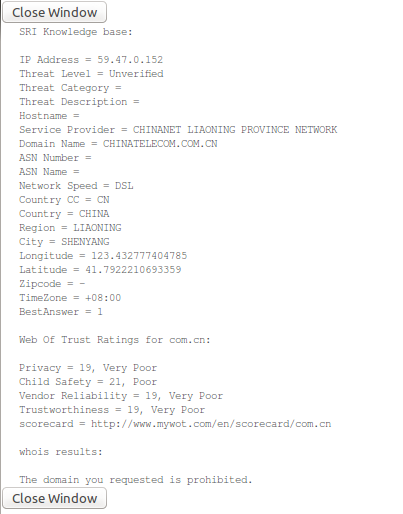
Whois Server/Client Address
Using this queries the "Whois" databases to see the organization that registered a particular IP address (if available).
Show Files in Flow(s)
Selecting this launches the Historical Flow and Payload Data Interface to show any recent flows and try to carve any files associated with this record. ‘’’Note’’’ that you must have a green light on the top right corner for this option to be available as the packet payloads are retrieved from the sensor. Refer to Historical Flow and Payload Data for details on this page.
Resolve Server/Client Address
This resolves the server/client address DNS for the record selected.
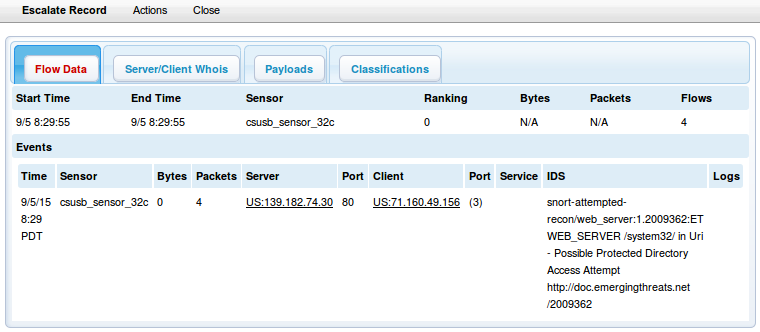
Escalate Records
This creates an escalation report for the flows selected. The report includes all events and payload data. The report can be emailed in text or .pdf format to create an incident reports summary.
Classify
This launches a Classify window pre-populating all the fields of the classification with the value of this record. See Event Classification for further details.
Filter by Server/Client
This changes the interface to only show events which include the specified IP address
Tune IDS
Using this allows for the creation of pass rules so that the sensor will ignore certain events in the future. The pass rule can be restricted to the specific addresses involved in the event or to all addresses (thus implicitly disabling the rule).
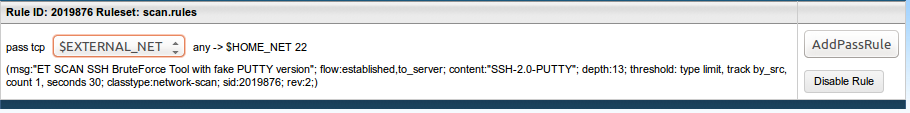
Rule Info
This launches the Rule Info interface for the Snort event selected.
Server/Client Address Historical Report
This option opens a new instance of the Historical Report page with a query to find all events matching the server address or client address for this particular record.
Block Server/Client
This inserts a block classification for the specified IP Address.
Map These/All Addresses
This launches the geo-ip map for either the addresses in the current flow or all addresses in the interface.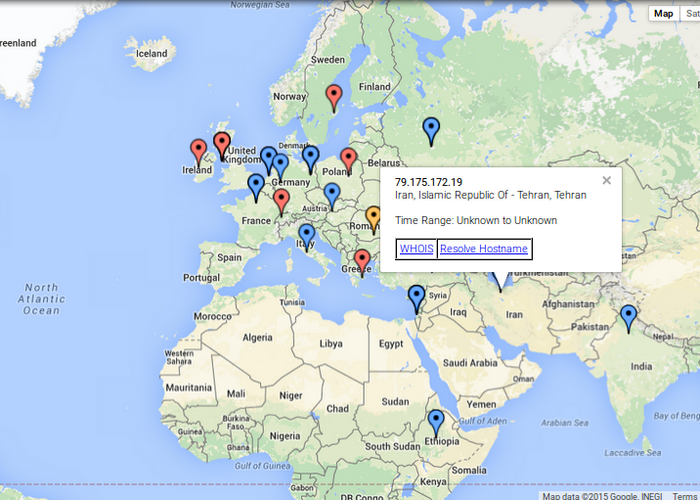
Scan Server/Client/Port
This initiates a vulnerability scan against the specified IP addresses and ports.
Annotate Rule/Server/Client
This adds the users comments to a database that is shared among all MetaFlows users.
| Previous Chapter | Next Chapter |
 1 (877) 664-7774 - support@metaflows.com
1 (877) 664-7774 - support@metaflows.com