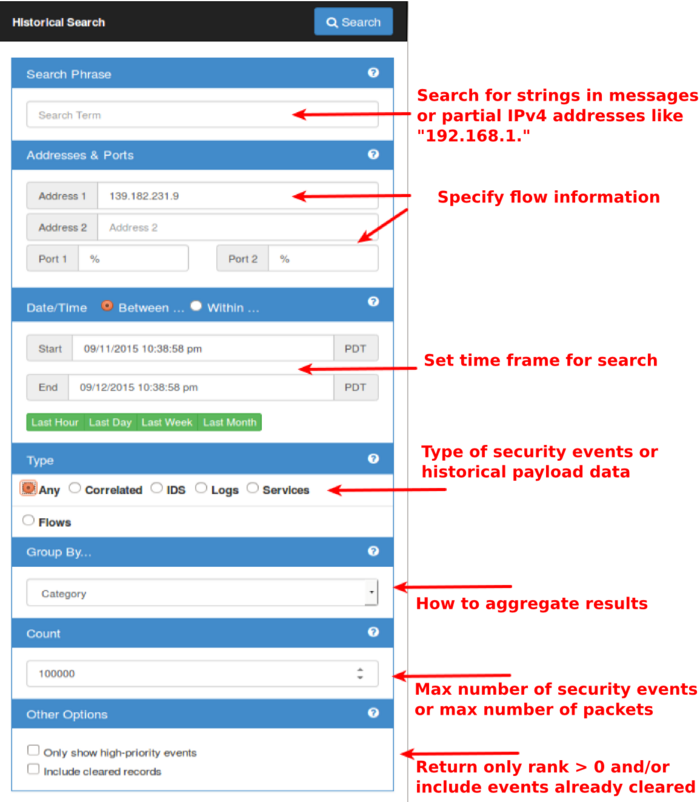
Search Events or Flows
From The MetaFlows Security System Documentation
The search interface pop-up can be used to search for specific events or historical flow and payload data. It will create a new browser window containing the results of the search. If no new window appears check for errors in the search parameters outlined with a red box.
- Search Phrase
- This is an events only search for a string in the event messages. It can also be used to search for partial IPv4 addresses such as 192.168.1.
- Address1/2 Port1/2
- Use this search for records with match specific IP addresses or ports. The order in which addresses and ports are entered is irrelevant since the query will return records with specified addresses or ports as either the server or the client.
- Date/Time
- This defines the time frame for the search.
- Type
- IDS events can be queried from individual rule files, event classifications or specific GID or SID.
- Syslog events can be queried by the categories or can be queried using a string search. In addition to the standard syslog categories, the following MetaFlows-specific events can be queried:
- File Inbound/Outbound: Any file transmission detected coming in our out of your network
- Tracker: Multi-session incident reports
- BotHunter: Dialog-based incident reports.
- mssBlock: SoftIPS blocking reports.
- ModSecurity events.
- Services: This searches for specific services that were discovered.
- Flows: This searches for historical flow and payload data. Flow data can only be searched by addresses and port, by time frame or priority.
- Group By
- Server/Source - This prevents aggregating the event data by the IP Address on the left of the report, thus reporting a summary of all events caused by these addresses.
- Client/Destination - Use this to prevent aggregating the event data by the IP Address on the right of the report, thus reporting a summary of all events caused by these addresses.
- Alert/MIME Type - This prevents aggregating by the event type (for events) or MIME type for flows. This results in aggregating the data by these characteristics.
- Category/Flow - Use this to prevent aggregating by event categories for events or source and destination addresses for flows. This results in aggregating the results by these characteristics.
- Best - This lets the system try to minimize the total number of rows and this mode can also be used to discover unforeseen data aggregations automatically.
- Count
- This limits the number of events or the number of packets returned, if flows is selected.
- Only show high-priority events
- This strictly retrieves high-priority events.
- Include cleared records
- If checked, this will display all events even when they have been cleared by yourself or another user.
| Previous Chapter | Next Chapter |
 1 (877) 664-7774 - support@metaflows.com
1 (877) 664-7774 - support@metaflows.com