User Identification
The MSS log management system is capable of associating host addresses to users by monitoring the login processes where a user identifies himself/herself to an authentication service such as Active Directory. Each time a user is successfully identified as using a specific host IP address, this information is logged and stored in the historical assets database. More importantly, whenever the sensor generate a security event for a specific internal host address, the user name of the individual currently logged in is also reported in the event message.
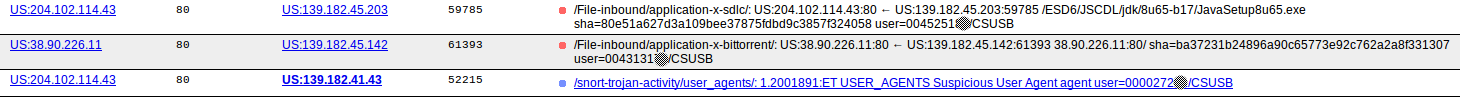
For example the screen-shot above shows that users 0045251XX, 0043131XX and 0000272XX from the domain CSUSB where logged in with IP addresses 139.182.45.203, 139.182.45.142, and 139.182.41.43 respectively and they generated the events shown.
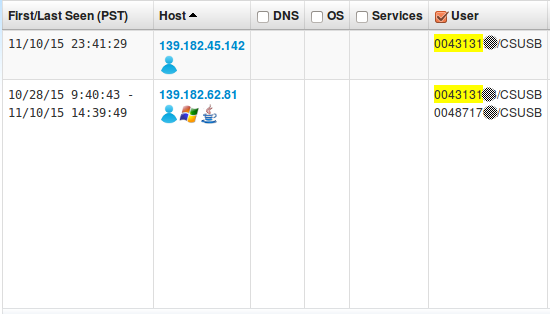
Looking at the historical assets database a quick search shows that user 0043131XX also used host 139.182.62.81. This host was also used by user 0048717XX.
Active Directory and Microsoft Exchange Support
The association of user names to IP addresses is supported by installing the MSS Log collector agent on Active Directory or Microsoft Exchange servers or individual Microsoft workstations. The Log collector gathers the Windows Event logs that provide the IP Address to user name mapping and forwards them to the NSM sensor for analysis. This information is then provided in both real time event streams and historical logs and reports.
To add this functionality simply choose option 2 or 3 when installing the MSS Windows Agent. This agent will forward the necessary Windows Event logs to the MSS sensor in an encrypted channel. This has also the added benefit that other important Windows log events will be recorded by the MSS thus providing log management for Microsoft systems.
 1 (877) 664-7774 - support@metaflows.com
1 (877) 664-7774 - support@metaflows.com